Amazon IAM Policies: Granting one user access to a S3 bucket
It may be easy to use the same master Access Key and Secret Access Key for all your apps using Amazon AWS, but it’s definitely not secure and recommended against.
That said, I had a little trouble writing the IAM policy granting a single user access to a single S3 bucket. I finally had time to sit down and figure it out today, and turns out - it’s pretty easy. Up to this point, I’m assuming that you’ve already created your user, but if you haven’t - the IAM management console is located here: https://console.aws.amazon.com/iam/home?#users.
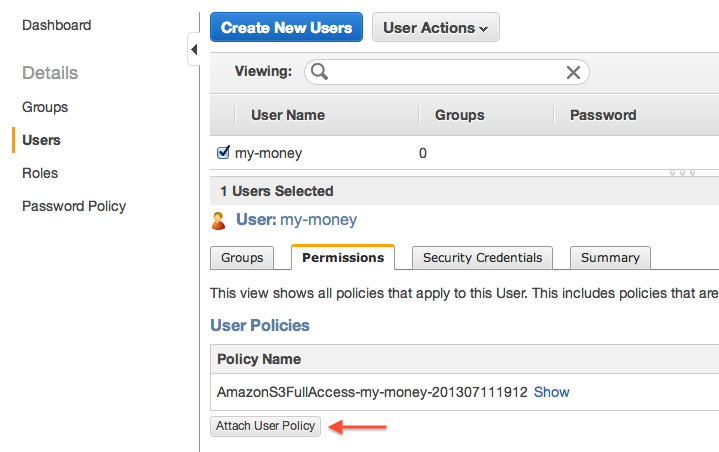
Once you’ve opened the “Permissions” tab of the user, click “Attach User Policy”.
 You’ll get a dialog with a bunch of choices - use the “Custom Policy” option, then click the “Select” button.
You’ll get a dialog with a bunch of choices - use the “Custom Policy” option, then click the “Select” button.
Here, you’ll enter the name of the policy (something descriptive) and the contents of the policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "s3:*",
"Resource": [
"arn:aws:s3:::bucket-name-here",
"arn:aws:s3:::bucket-name-here/*"
]
},
{
"Effect": "Allow",
"Action": "s3:ListAllMyBuckets",
"Resource": "arn:aws:s3:::*"
}
]
}
Of course, you need to replace “bucket-name-here” with the name of the bucket that you want to grant access to.
If you’re using a console or GUI tool ( Transmit recommended :) ), you’ll need the "Action": "s3:ListAllMyBuckets" section that’s included in the sample, but if you’re accessing your bucket programmatically, it’s not required.
Source: AWS Security Blog / “Writing IAM Policies: How to grant access to an Amazon S3 bucket”